Application of P2P remote access technology in security video surveillance
The development of network, chip, and Internet of Things technology has promoted the introduction of security video surveillance products into ordinary households. Individual consumers buy an ordinary WiFi camera and use it to visit home, see the elderly, see children, watch pets, and remotely monitor mobile apps anytime, anywhere. Play back the video. It is cheap, powerful and easy to use.
One of the important network technologies is P2P remote access. Once upon a time, video surveillance needed to realize networked remote surveillance, and there were many restrictions. If you don’t have a static IP on the public network, you can connect directly through an IP address. However, based on the reality of China’s telecommunications industry, it is very expensive for ordinary home users to obtain a static IP address on the public network.
Without the public IP, you can only go the other way, do port mapping in the router and bind dynamic domain name (DDNS) (see the article “Application of DDNS(dynamic domain name service ) in security“). The problem with this method is that for ordinary users, the port mapping method is more complicated and difficult to master. At the same time, the stability of dynamic domain names is relatively poor.
P2P remote access technology solves the above pain points, is convenient, simple, stable and reliable. The core of P2P remote access is P2P penetration, peer-to-peer penetration, Peer to Peer. After the front-end security camera passes a certain processing method, it actively establishes a connection with the requesting client (mobile app) to send the video stream.
Working principle
The main working principle of P2P in the current system is to transplant a P2P penetration assistant program into the front-end camera. The P2P penetration assistant program will register the device with the platform server, and the server can also identify whether the device is online. At the same time, the P2P penetration assistant program will exchange necessary information with the server to realize network analysis and connection establishment functions. The working principle of P2P penetration is as follows:
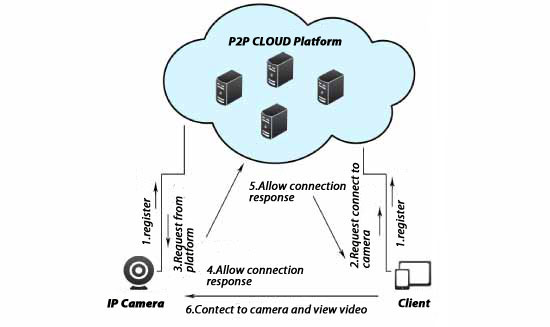
P2P penetration needs to face three possible network situations: 1. The camera and the client are in the same local area network. This is the simplest, direct connection within the LAN without penetration. The real-time and smoothness of network transmission can be guaranteed; 2. The camera and the client are not in the same local area network, and P2P penetration can be successful. I will talk about it in detail below. 3. It cannot penetrate successfully, and the method of streaming media forwarding needs to be used at this time.
Penetration method
It is possible to achieve P2P penetration, and the probability of success is relatively high. The UDP protocol has a relatively high success rate for data transmission through NAT, which is close to 100%. However, there are some situations in which TCP cannot achieve traversal, which is mainly limited by the port mapping mechanism of the router.
To achieve P2P penetration, a P2P penetration server needs to be deployed on the Internet (with a fixed domain name or IP), and the server will assist the network camera and client to achieve P2P penetration. Some servers can also realize the function of streaming media forwarding when TCP cannot traverse, so as to ensure that data communication can be realized between the two.
Since the P2P penetration server is different from the streaming media forwarding server in the security monitoring system, it mainly conducts signaling interaction and does not forward media data. After assisting in opening up the data channel, the corresponding network cameras and clients will no longer occupy the server bandwidth and With the processing power, a P2P penetration server can access a large number of network cameras and clients.
Usually the network camera has a unique ID and is registered to the P2P server through this ID. When the client wants to access the corresponding network camera, it also needs to register to the P2P server first and submit the ID of the corresponding network camera. The server will find the corresponding network camera and assist the network camera to penetrate between the client and finally get through one. Point-to-point data transmission channel. After that, the two can perform normal media and signaling interaction.
In order to achieve more effective management, the server can authenticate device access.
PC access network camera.
To access a network camera from a PC, you can first visit a web page and input the serial number of the network camera.
The web page loads a control. After the control is penetrated through the P2P penetration server and the network camera corresponding to the serial number, it transmits signaling and media data through reliable UDP. The control provides functions such as video browsing, intercom, pan/tilt control, parameter query setting, etc.
Mobile phone accesses the network camera.
Due to the different platforms of mobile phones, corresponding clients or plug-ins need to be developed separately to achieve similar functions as PC access. But the principle is the same. After the penetration is achieved through the P2P server and the network camera corresponding to the serial number, the signaling and media data are transmitted through reliable UDP. Since the open source P2P penetration library is portable, the same P2P penetration function can be achieved in LINUX, IOS, Android, etc.
Regarding the specific penetration code, you can search by yourself if you need it, and there are third-party penetration middleware services on the Internet. There is an attached list at the back for reference. The core of penetration is to choose different strategies for different network environments. That is, it is clear where the device is located on the network. A concept of NAT is involved here.
Because IPv4 addresses in the Internet are not enough, the NAT function is introduced. NAT, Network Address Translation, that is, network address translation. This method is to use a router with NAT function between the internal network and the external network. The router can assign a public network IP, and any internal machine communicates with the external network through this public network IP. This is a good solution to the problem of limited IP addresses. But the problem ensues. Many network protocols cannot pass NAT. At this time, we need to traverse NAT, that is, P2P or NAT.
The premise of NAT penetration is to determine the type of NAT. Generally speaking, NAT is divided into static NAT and NAPT. Static NAT is easy to understand, that is, one internal network IP corresponds to one public network IP. NAPT is much more complicated. NAPT is the port multiplexing technology. It not only needs to convert the IP address, but also needs to perform port conversion at the transport layer. The specific performance is that there is only one public network IP externally, and different devices on the internal network are distinguished through different ports.
In actual use, NAPT accounts for the vast majority. NAPT can be divided into 4 types, namely:
- Full cone type (IP address and port are not restricted)
- Restricted cone type (IP is restricted, ports are not restricted)
- Port restricted type (IP address and port are restricted)
- Symmetric (one request corresponds to one port)
Limitations of P2P access
- There is a limit to the number of users who can access the same device online at the same time. Since the P2P penetration is successful, both the device and the client directly perform video streaming. Therefore, the number of users accessing the camera at the same time will affect the user’s viewing experience. One is because the hardware performance of the camera itself is not enough to support too many users to visit at the same time, and the other is because the number of people visiting at the same time is large, and the uplink bandwidth demand of the camera will be greater. The uplink speed of ordinary household broadband is difficult to support a large number of users to visit. . Therefore, manufacturers generally limit the number of users that can access the device at the same time. For example, the number of accesses is limited to 3, and users who exceed this number will not be able to preview in real time.
- What should I do if the penetration is unsuccessful? No P2P technology can guarantee 100% penetration success. For those that cannot successfully penetrate, we can only choose to use streaming media forwarding at this time. This method has certain requirements as a server for streaming media forwarding.
Streaming media forwarding server requirements
In streaming media forwarding services, the network bandwidth has a greater impact on the service, followed by memory and CPU.
| Number | CPU | RAM | System | Remark |
| 1 | Dual core 2.4G | 4G | Win 2003/2008 32Bit | Supports simultaneous online viewing of 500 channels. |
| 2 | Dual core 2.4G | 8G | Win 2003/2008 32Bit | Supports simultaneous online viewing of 1000 channels. |
| 3 | Octa-core 4G | 32G | Win 2003/2008 32Bit | Supports simultaneous online viewing of 2000 channels. |
The network bandwidth is calculated based on the number of devices accessed online in real time. If the user has no requirements for the standard definition and high definition of the viewing picture, the bit stream output of the device can be reduced to reduce bandwidth consumption.
WebRTC technology
Using WebRTC can easily achieve P2P penetration by UDP, and it perfectly supports three methods of direct connection, penetration, and forwarding, with a high success rate. But it also has its limitations. The WebRTC technology will be specifically introduced later, here is temporarily put forward.
How to troubleshoot P2P remote access failure
In actual use, when I often encounter P2P access, the display device is offline or cannot be accessed. How should we troubleshoot and solve it?
First of all, with regard to the principle that network equipment can support P2P access, we had better understand it, so that we can grasp the reasons for P2P access failure from the overall perspective and find a solution.
The entire connection process has three parts: the front-end equipment, the cloud platform server, and the back-end access client. The core problem is that the front-end equipment can achieve network penetration and send the video stream to the client. If we find that the cloud cannot be accessed, we will look for the problem and the cause from these three parts.
Device
Whether the device is properly connected to the internet. The device is connected to a switch or router through a network cable, and the router is connected to the external network.
Possible problems and troubleshooting methods:
- Whether the external network is normal and able to access the Internet. Check the network cable and the corresponding network port of the device. Whether the computer or mobile phone in the local area network can be connected to the external network.
- Whether the network parameter settings of the device are correct. Whether the IP address, subnet mask, gateway, DNS settings are consistent with the configuration in the router. Consider whether the IP addresses conflict and whether the device network segments are the same. Among them, the device’s DNS is especially the device’s DNS. Domestically, the device’s DNS in the router can be used directly. Foreign users recommend using some public DNS, such as 8.8.8.8. This makes it easy for the device to quickly connect to a nearby cloud server deployed overseas.If the router has the DHCP function enabled, you can try the device to use DHCP to automatically obtain network information.If you still cannot successfully access the cloud, you can consider modifying the default port of the device. Mainly web access port, data transmission port and RTSP streaming media port.If the device has its own network, cloud access detection function, you can use this function to detect and find the problem.After resetting or modifying the network parameters, it is generally necessary to restart the device.
- Whether the device supports the P2P cloud access function, or whether the cloud access function is enabled. In addition, whether the cloud function of the device is upgraded, you need to upgrade the new device firmware.
P2P cloud service platform in the cloud
This part has nothing to do with the user, but it is understood that we can better understand the P2P cloud function, so that we can locate the problem of unsuccessful cloud access.
After reading the above introduction, it should not be difficult to understand that the cloud service platform mainly serves as a bridge between front-end devices and back-end clients. The stability of the cloud platform, the success rate of P2P penetration, and the speed of connection will all affect the success rate and experience of users’ P2P cloud access.
Stability means considering cloud platform architecture, physical security, network bandwidth, number of servers, performance, server deployment around the world, CDN acceleration, etc.
The success rate of P2P penetration, that is, whether the P2P penetration technology used is reliable, whether the penetration rate is high, and suitable for different network environments. Are there any alternatives for unsuccessful P2P penetration? For example, when P2P penetration is unsuccessful, a manufacturer uses video stream forwarding to connect to the device, which can improve the success rate of the connection between the device and the client. (If there is an update of the P2P penetration library, the device firmware and mobile phone app should be updated in time)
The speed of connection, as mentioned earlier, changing the DNS of the device to 8.8.8.8, for foreign users, may be able to connect to the nearest cloud platform faster. The current network video surveillance manufacturers, including some that provide third-party cloud access platforms, are basically Chinese. Most P2P cloud platform servers are deployed in China. When domestic users use the P2P cloud function, they feel that the connection is faster, more stable and reliable. This is what we must consider when setting up a cloud platform. Whether to deploy servers in major countries and regions around the world, CDN acceleration, and network optimization, so that local users can access the cloud platform faster.
Client
Access terminals generally include web pages, mobile apps, and computer clients. It can support us to connect to the front-end equipment through P2P.
Generally, the possibility of problems on the client side is very low. There are several aspects that need attention:
- Update mobile apps, computer clients, and web access controls in a timely manner.
- Mobile app. Whether the mobile phone supports hardware and software video decoding, whether the mobile phone performance supports video decoding display, whether to grant the corresponding authority of the mobile app, etc.
- Whether the client is connected to the external network.
Security camera P2P platform
| NO. | APP | Developer | Serial number(For example) |
| 1 | XMeye,iCsee | Xiongmaitech | e3cddc089a825759 |
| 2 | EseeCloud3,VR CAM,IP PRO | JUAN | 1589902825 |
| 3 | seetong | Topsee | 9847002 |
| 4 | Yoosee | Gwell | 3836362 |
| 5 | IPC360 | Puwell | 406A8E16CF73 |
| 6 | Danale | Danale | 44f5a7ebb1ee89853a7dcbac621b6249 |
| 7 | Goolink | Vnow | |
| 8 | UMeye | UMeye | |
| 9 | p2pcamlive,P2PViewCam | TUTK | |
| 10 | V380 | Macro video | |
| 11 | NVSIP | Sunywo | |
| 12 | YCC365 Plus/PixPlus | closeli | |
| 13 | i-Cam,Ubell,Ubox | uBia | |
| 14 | CareCam | HuiYun | |
| 15 | Tosee | Tocoding | |
| 16 | CamHi | CamHi | MMMM-102311-BDCCF |
| 17 | FINDCAM Max | ZScam | BYWDUJWZHZNS6MVR2YZA |
| 18 | Tuya,smart life | Tuya smart | 6c97d7ef8fb7786972cvsg |
| 19 | YI IoT | YI techonlogy | |
| 20 | EZVIZ | Hikvision | |
| 21 | Imou life | Dahua tech |
More P2P and security video camera app and platform please visit here.
P2P penetrates third-party middleware
| No. | P2P Platform |
| 1 | peergine |
| 2 | pptun |
| 3 | houhangkeji |
| 4 | gizwits |
| 5 | vveye |







Leave a Reply
Want to join the discussion?Feel free to contribute!